
This post summarizes the key concepts of Dockers and related tools. Photo by Max Williams on Unsplash.
Docker
Container is designed to provide isolation. Docker is a framework that implement its own containers. Containers are mainly based on the following concepts.
chroot
chrootis a way to isolate a directory. Using this command, you can set a target directory as the root directory.- After getting into that dir using
chroot, you cannot access anything out of the dir. (But it’s not a real secure sandbox, explained below). - Consider a use case. A
makebox.shcontains the following content.1
2
3
4
5
mkdir box
mkdir box/bin
cp -v /bin/bash /home/class/box/bin
cp -v /bin/ls /home/class/box/bin
Then, use this command sudo chroot $HOME/box /bin/bash, we will get into the box dir, and it is able to use the tools that we copied like ls.
In fact, chroot achieves this simply by prepending the new root path to any path starting with /. Therefore, chroot does not provide a truly secure sandbox. A well known ‘problem’ is that a root user can exit the chroot environment, therefore, if a hacker finds out that it’s in a chroot environment, he/she may and exit and be able to enter the real root directory. Fortunately, Docker containers don’t have this problem since it uses namespace to isolate file systems.
cgroups
cgroups is short for Control Groups, which provides the access controls over system resources. cgroup is developed in 2006 by 2 google engineers. In 2008 it was added to the Linux kernel 2.6.24. Used by many container projects, Docker, LXC.
Specifically, cgroup can be used to
- limit resources: Groups can be set to not exceed a configured memory limit.
- prioritize: Some groups may get a larger share of CPU utilization or disk I/O throughput.
- measure the resource usage of a group.
- control groups: freezing groups of processes, their checkpointing and restarting.
namespace
Namespace enables a process to have a different view of the system than other processes.
The 7 namespaces are Cgourp, IPC, Network, Mount, PID, User, UTS (host name and NIS domain name). One can use these namespaces to isolate corresponding resources.
For example, two processes in two different network namespaces may run on the same port number, processes in different PID namespaces may have the same PID. In fact, Linux uses two PIDs to identify a process in a new PID namespace, one is global PID and the other one is the new namespace PID. However, the process in the new PID namespace cannot see its global PID, only the parent process knows it.
As the same, other namespaces isolate a specific global resource and restricts access of a inner process to its own sandbox.
Summary
chrootrestricts access to the filesystem.cgrupsrestricts access to the system resources.- namespaces provide 7 types of isolation.
Docker vs VMs
The following figure clearly shows the differences of docker and virtual machines when achieving isolation. On the left side, we can see that all of the docker containers share the same engine, and the docker engine is based on the host OS. While, VMs isolation is achieved on the hardware-level: Hypervisor.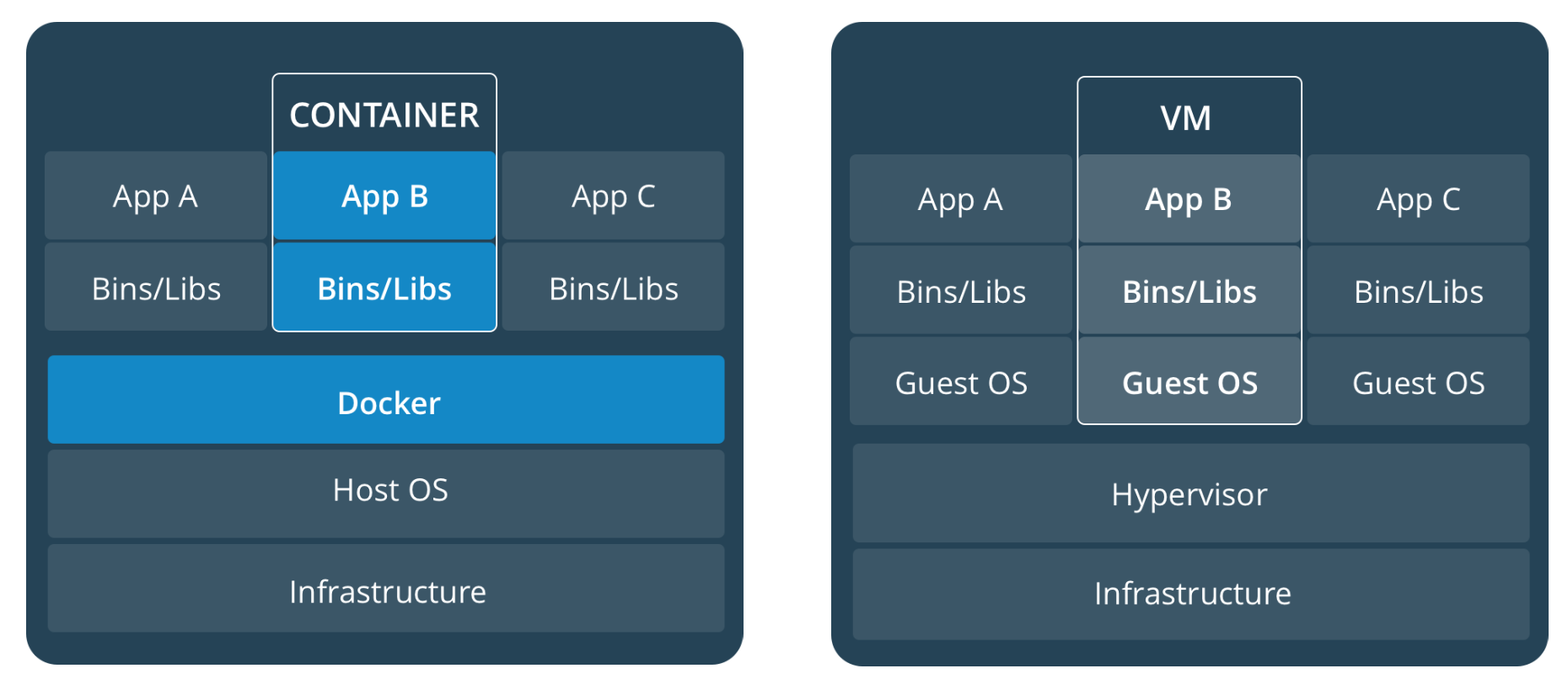
The pros and cons over docker and VMs are shown in the following figure.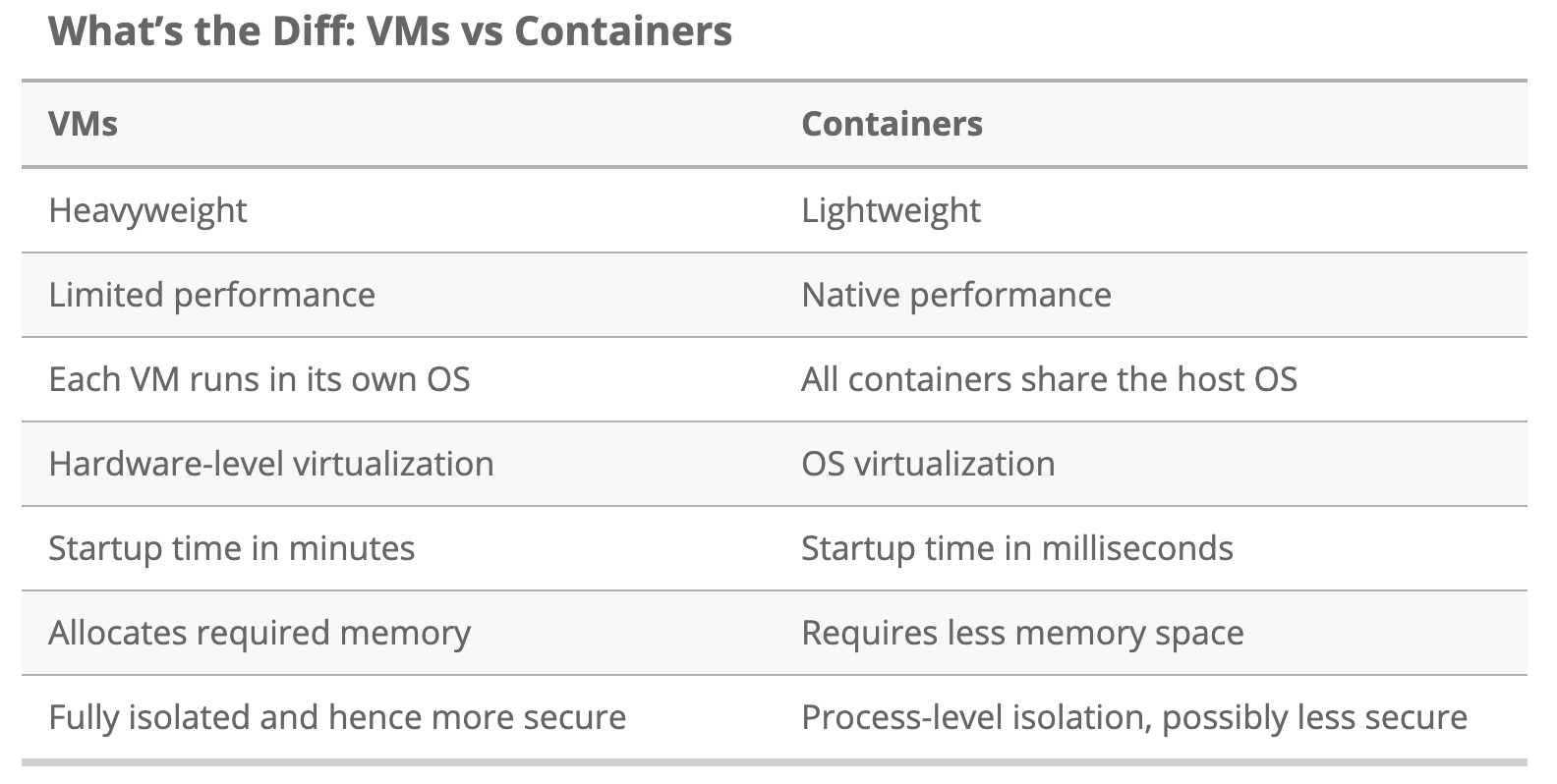
Related tools
Docker-compose
In some scenarios, we might need to start a lot of containers at once. But doing this on cmd causes a lot of time, since we need to enter the commands manually and wait for the last one to finish. That’s why we need docker-compose.
Docker compose is a tool for defining and running multi-container Docker applications. With Compose, you use a YAML file to configure your application’s services. Then, with a single command, you create and start all the services from your configuration.
Kubernete
Different from compose, Kubernete is a container orchestration framework developed by google, you may use the kubernete configuration file to support container connections on different host machines. You might want to look at this post to further discriminate different docker-related tools.
Kubernete abandons Dockers ?!
Recently, Kubernetes is deprecating Docker as a container runtime after v1.20. It’s because Kubernetes don’t need the nice CLI interaction features that Docker has. Previously, Kubernetes have to use an extra tool Dockershim as a way to interact with Docker, which is quite redundant. Therefore, instead of interacting with Docker, kubernetes decide to directly interact with containerd.
Then, what is containerd? In fact, containerd is a important platforms that provides the abstract-level APIs to push and pull functionality as well as image management; to create, execute, and manage containers and their tasks. In other words, Kubernetes decide to directly talk with the core of Docker so that a step can be saved.
Reference and recommended reading.
[1] What is containerd?
[2] Kubernetes is Removing Docker Support, Kubernetes is Not Removing Docker Support.
[3] Don’t Panic: Kubernetes and Docker.
[4] Docker security.
[5] chroot, cgroups and namespaces — An overview.
[6] What’s the Diff: VMs vs Containers.
[7] Docker overview.
[8] Overview of Docker Compose.